Application Security Software Designed to Identify & Fix Security Weaknesses in Code
Checkmarx operates in the exciting field of application security (AppSec) and is considered one of the pioneers in the field and a global leader. The automatic platform of Checkmarx detects and warns of security holes in software throughout all development stages, from writing the first line to the testing stage.
Checkmarx became a unicorn a year ago, with its purchase in April 2020 by the American investment fund Hellman Friedman for almost 1.2 billion dollars. According to the company, since then many exits and issues have been reported in the Israeli ecosystem, but Checkmarx will be remembered as the first giant deal that “injected” some optimism into local high-tech at the beginning of the Covid-19 pandemic.
-
Company: Checkmarx
-
Field of Activity: Cyber Security
-
Website: www.checkmarx.com
-
Project: A code security testing system for programmers
-
Year: 2018-2021
-
Duration: two and a half years
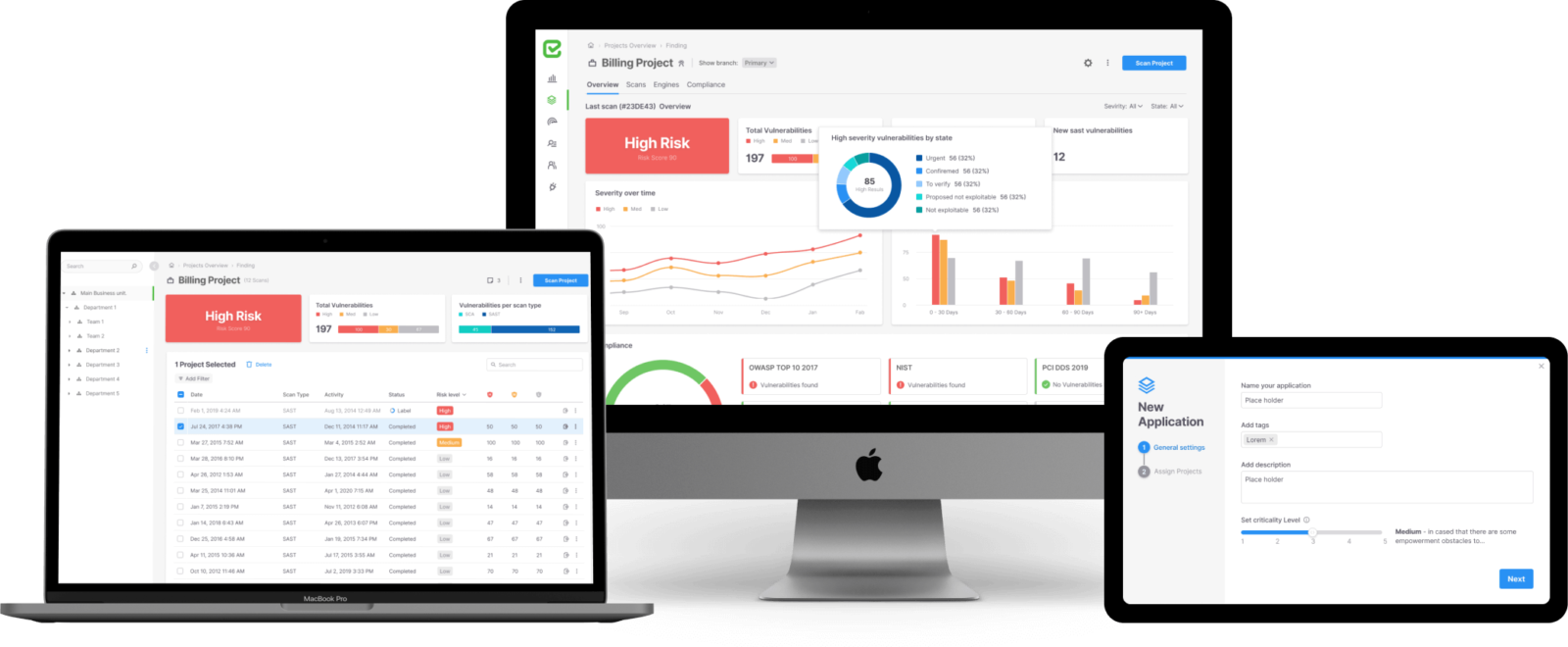
A small taste of examples from the system screens
Checkmarx – identifying weaknesses in third-party software
With the adoption of the open source world, many organizations face data security challenges when using code or third-party dependencies. With Checkmarx’s product, organizations can better monitor, assess and remediate the weaknesses in the authorization set of third-party entities in order to test their feasibility for integration into your system.
This video presents a detailed explanation of the company’s product and details the system itself (UI), the division into packages, the risks, performing a weakness analysis and a legal analysis.
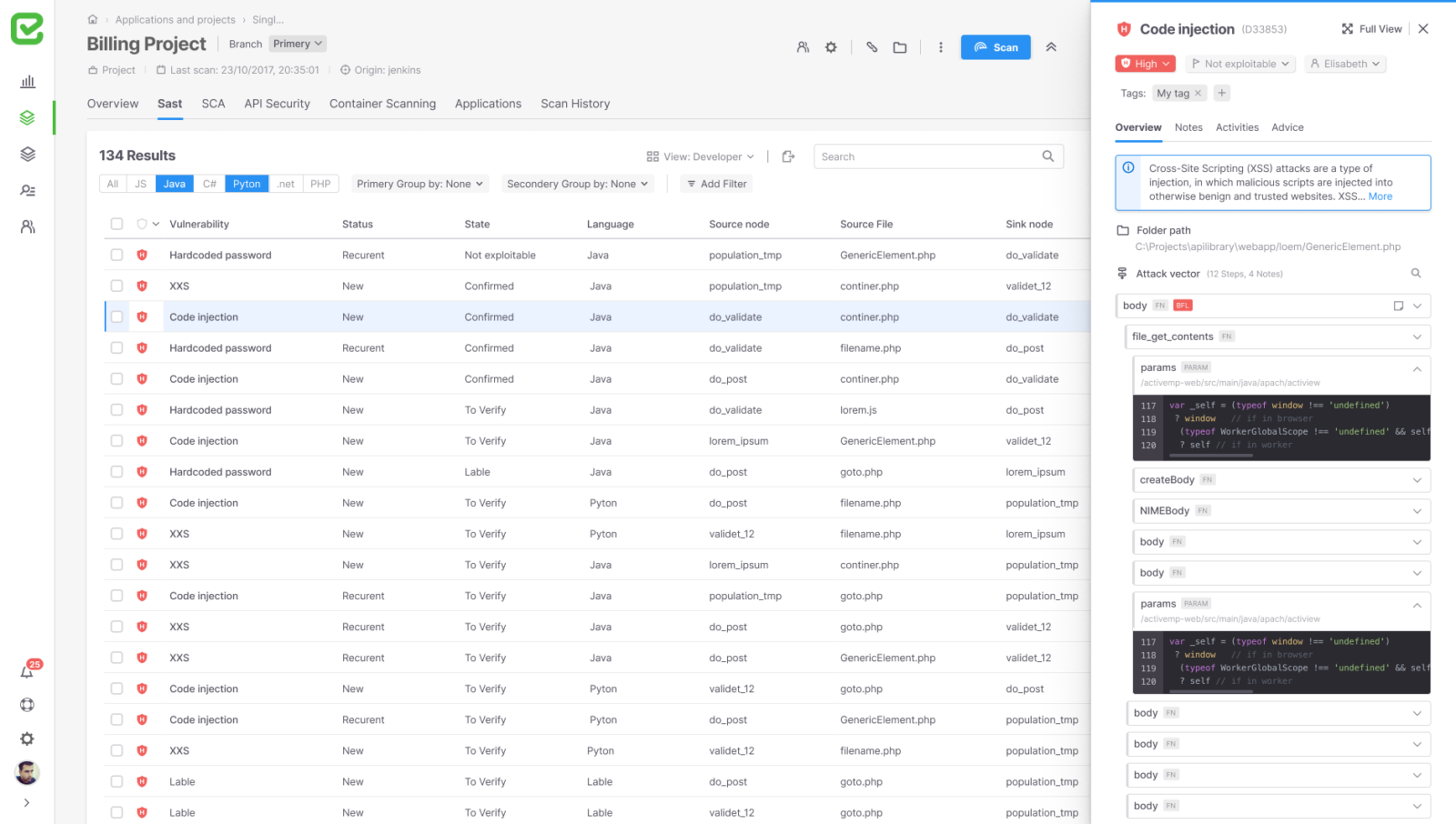
Project view
The screen shows the list of vulnerabilities at the project level, the table can be filtered in a variety of ways and you can enter each line and get concise information about it in a side panel that opens when you click.
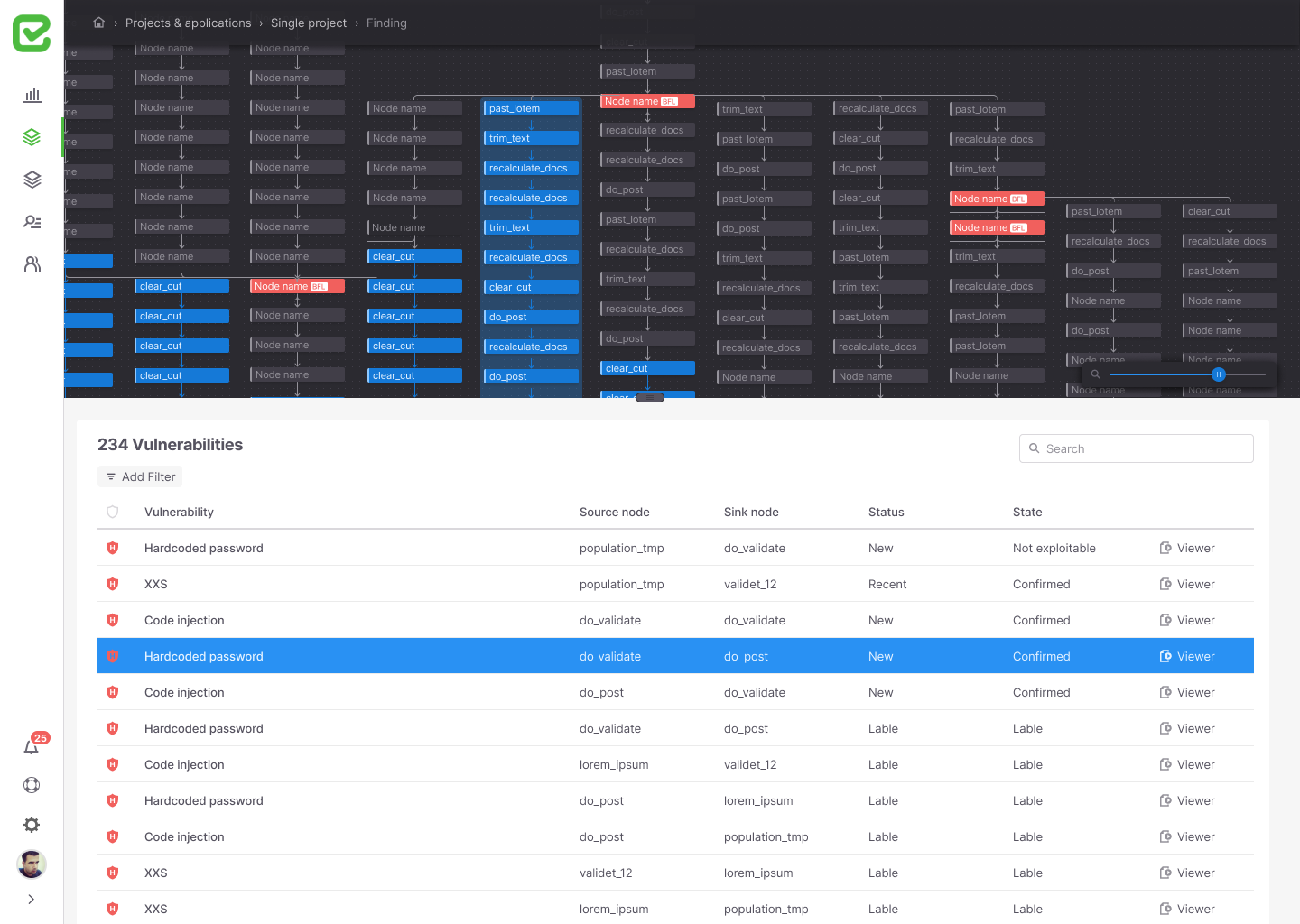
Tree look
The vulnerabilities can also be presented in the hierarchical structure that is reflected in a system tree that allows to identify where there is a particular vulnerability whose impact is central and therefore it is better to deal with it first.
Clicking on an element in the tree displays additional information in the table below using a split screen structure.
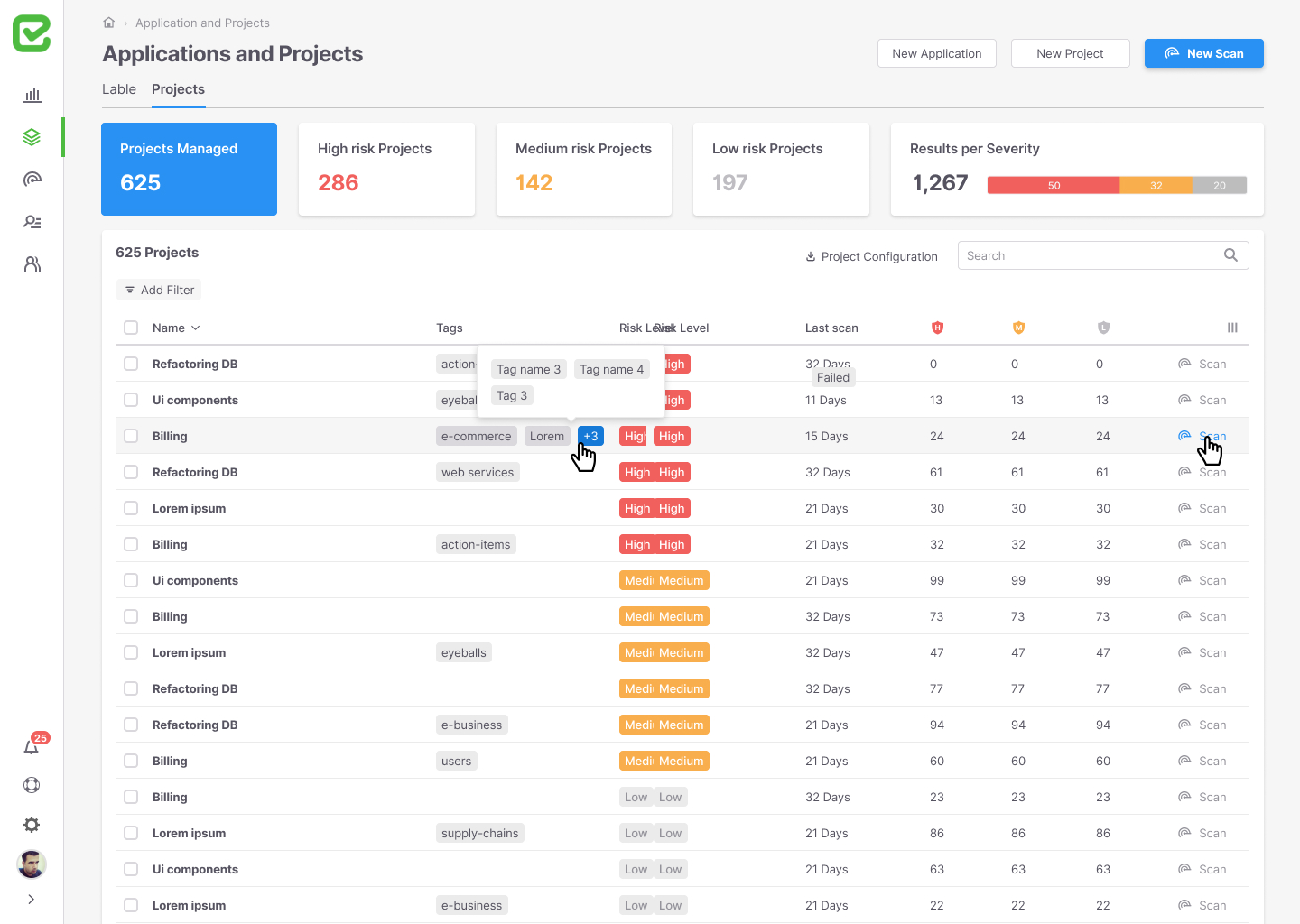
The list of projects
A screen showing all the open projects in the system, with search and filter capabilities. The upper part is filled with an analytical summary of the main information for the user.
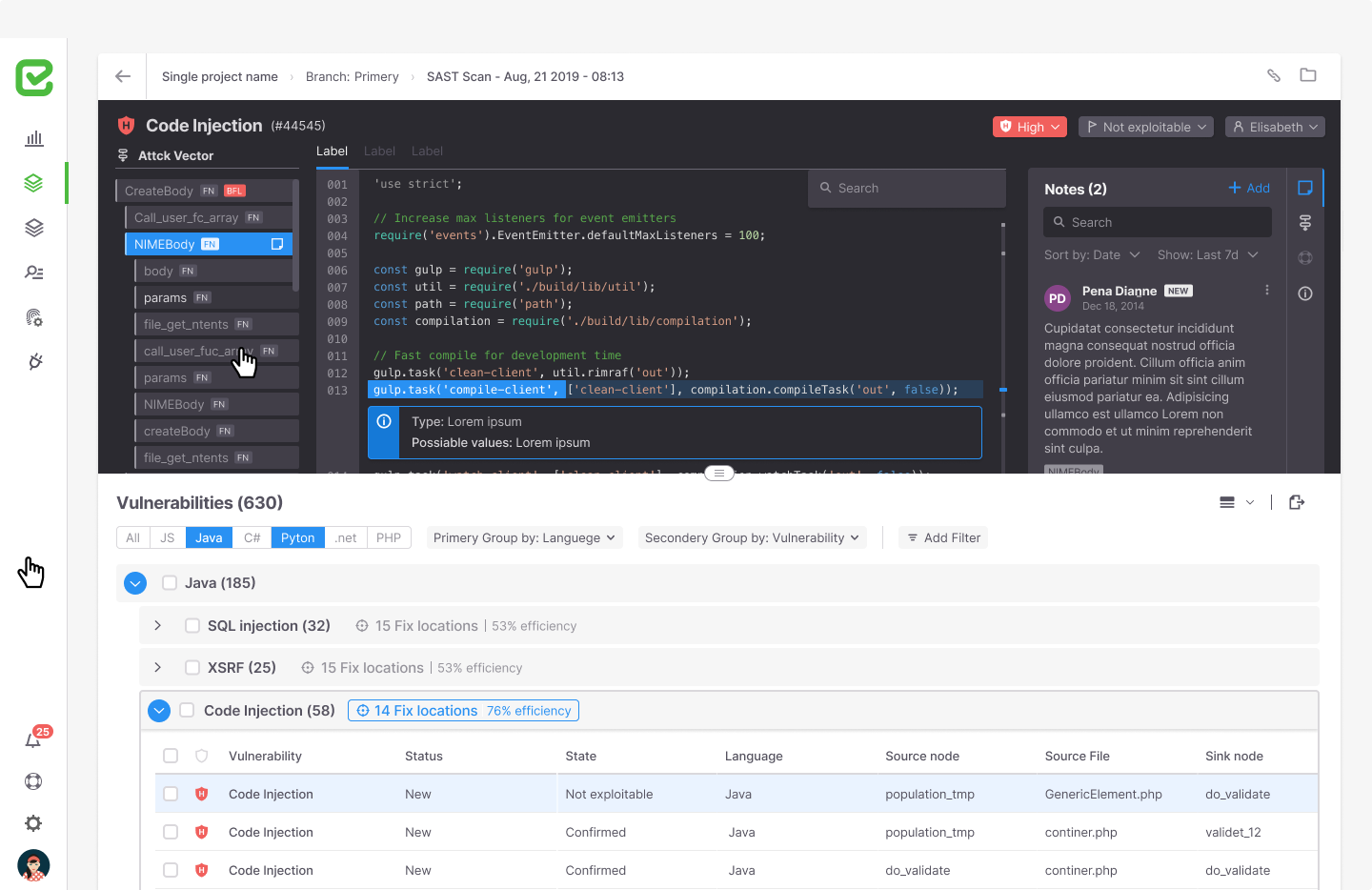
Screen vulnerabilities at code level
The screen shows the list of vulnerabilities at the code level and the specific location where the fault or problem occurred. In addition, there is an information envelope for the user that allows them to receive instructions on how to solve the problem.